IT Decision Making
The Need for Constant Communication How do business leaders make decisions regarding IT? Do they have a formal process, or is it informal word of...
2 min read
 Wade Yeaman
:
Feb 18, 2024 12:11:35 PM
Wade Yeaman
:
Feb 18, 2024 12:11:35 PM

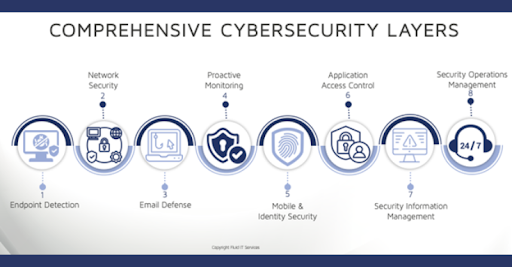
Cybersecurity is now the primary concern for businesses of all sizes. At Fluid IT, ensuring security is paramount for us and our clients. What many business owners, managers, and employees don’t know is just how much happens behind the scenes. Unfortunately, security only seems to become top of mind when there is an incident, a pain point that impacts the business that they would really rather not be dealing with.
A peek behind the curtain reveals that cybersecurity demands continuous review and enhancement. Fluid's security measures typically go unnoticed by the user, aligning with our goal to maintain seamless productivity. Although rare, there are instances where we feel additional communication is warranted, even though the business and end-user are not impacted.
I'd like to share insights on recent security activities, focusing on incident identification, remediation, and prevention.
Recently, our team countered brute-force attacks aimed at accessing company networks. This was a broad-based attack, knocking on every door it could find and trying to get in. This widespread attempt was quickly neutralized thanks to our alert systems and engineering team. It's crucial to understand that this wasn't a targeted attack but part of a broader threat landscape.
Following this, we've taken lessons from the attack to bolster our security framework. Cybersecurity threats are constant, necessitating perpetual vigilance from our team to ensure our client’s businesses continue to operate without disruption.
Diving deeper into a specific incident, our Security Operations Center (SOC) alerted our security team at 9:44 PM on a Monday about a login from an unfamiliar device. A closer look revealed a legitimate user had accessed his Microsoft 365 account from a personal device, not one issued by work, and had not logged out. Such an oversight could have severe consequences. An open Microsoft 365 session provides not just access to emails, but also to sensitive company data in SharePoint, files in OneDrive, and beyond. If someone else were to use that device, or if it were stolen, they'd have unrestricted access to a vast amount of confidential information.
In this case, even though the user was not intentionally trying to create an incident, our security team immediately blocked the user from any future sign-ins, reset his password, forced logout of all systems, and kept it in that state until the user reached out to inquire about lack of email, Teams, file access, etc. This hopefully became a learning lesson for that user.
The takeaway is that threats are omnipresent, attempting access round-the-clock. While our security team's efforts might often go unrecognized, their relentless work is crucial for uninterrupted operations.
In closing, the landscape of cybersecurity is ever-evolving, with threats becoming more sophisticated every day. Our dedicated team at Fluid IT is committed to safeguarding your business with state-of-the-art security measures, vigilant monitoring, and proactive responses to potential threats. Trusting us means not just preventing incidents but also ensuring peace of mind knowing your data and operations are secure around the clock. Don't wait for a breach to realize the importance of robust cybersecurity. Contact Fluid IT today and fortify your defenses. Let us be your partner in navigating the complex world of cybersecurity, because your security is our top priority.

The Need for Constant Communication How do business leaders make decisions regarding IT? Do they have a formal process, or is it informal word of...
XSP Defined Cybersecurity is the predominant concern of both small and large businesses. Therefore, securityis a top priority for Fluid IT and all...

Cyber Protection for Your Healthcare Organization Is your healthcare organization's cybersecurity keeping you up at night? Watch this exclusive Fluid...